radio frequency rfid security tags It's all a bit more complex than I've made it sound so far because there are, in fact, two quite different types of RF tags and they work in a slightly different way. Often the term "RFID" is loosely used to . See more Step 2: Tap “Buy Beep Load”. Step 3: Pick the Beep Card account you want to .
0 · ultra high frequency rfid tags
1 · ultra high frequency rfid
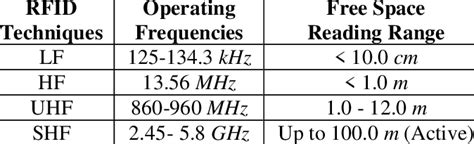
2 · rfid frequency chart
3 · highfid radio frequency tags
4 · disposable high frequency rfid tags
5 · difference between rfid labels
6 · 13.56 mhz rfid tags
7 · 100piece iso15693 13.56mhz tags
Smartphones are the best example of active NFC devices. Card readers in .
Radio or wireless is a way of transmitting energythrough empty space—that is, instead of using a wire cable. The energyis carried by invisible waves of electricityand magnetism that vibrate through theair at the speed of light. The basic science and the practicaltechnology of wireless communication was developed in . See moreImagine your mission is to design an anti-shoplifting device usingsome old radio sets you found in the garage. You could build something a bit like aradar (with a combined radio transmitter and . See moreIt's all a bit more complex than I've made it sound so far because there are, in fact, two quite different types of RF tags and they work in a slightly different way. Often the term "RFID" is loosely used to . See moreRadio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder called a tag, a radio receiver, and a transmitter. When triggered by an electromagnetic interrogation pulse from a nearby RFID reader device, the tag transmits digital data, usually an identifying inventory number, back to the reader. This number can be used to track inventory goods.
A pulsed beam of radio waves from the transmitter strikes the tag, making it give off a precise frequency radio signal. The receiver picks up the signal, verifies that it's at the correct frequency, and then sets off the alarm.Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder called a tag, a radio receiver, and a transmitter.
RFID (radio frequency identification) is a form of wireless communication that incorporates the use of electromagnetic or electrostatic coupling in the radio frequency portion of the electromagnetic spectrum to uniquely identify an object, animal or person. This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks.

RFID stands for radio-frequency identification. A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks. What are RFID security tags? Standing for Radio Frequency Identification, RFID tags are small microchips which send a radio signal to a receiver. And when we say small, we mean it! Because RFID tags are so basic and contain such little information (such as price/SKU number) they can literally fit onto a sticker on the back of a label.
This bulletin provides an overview of RFID technologies and recommends practices for initiating, designing, implementing, and operating RFID systems in a manner that mitigates security and privacy risks.RFID readers are devices that use RFID Antennas designed to capture and interpret the radio waves emitted by RFID tags. The antenna sends out a Radio Frequency (RF) signal that energizes the tag, enabling the tag to reflect back its unique ID code, and receives the reflected signal, which is subsequently decoded by the RFID reader to identify .radio-frequency identification (RFID), method of wireless communication that uses electromagnetic waves to identify and track tags attached to objects, people, or animals. The attached tags, called RFID tags, store digitally encoded data that can be read by an RFID reader.
A pulsed beam of radio waves from the transmitter strikes the tag, making it give off a precise frequency radio signal. The receiver picks up the signal, verifies that it's at the correct frequency, and then sets off the alarm.Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder called a tag, a radio receiver, and a transmitter.

RFID (radio frequency identification) is a form of wireless communication that incorporates the use of electromagnetic or electrostatic coupling in the radio frequency portion of the electromagnetic spectrum to uniquely identify an object, animal or person.
This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks. RFID stands for radio-frequency identification. A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks.
ultra high frequency rfid tags
What are RFID security tags? Standing for Radio Frequency Identification, RFID tags are small microchips which send a radio signal to a receiver. And when we say small, we mean it! Because RFID tags are so basic and contain such little information (such as price/SKU number) they can literally fit onto a sticker on the back of a label.
This bulletin provides an overview of RFID technologies and recommends practices for initiating, designing, implementing, and operating RFID systems in a manner that mitigates security and privacy risks.RFID readers are devices that use RFID Antennas designed to capture and interpret the radio waves emitted by RFID tags. The antenna sends out a Radio Frequency (RF) signal that energizes the tag, enabling the tag to reflect back its unique ID code, and receives the reflected signal, which is subsequently decoded by the RFID reader to identify .
ultra high frequency rfid
$12.29
radio frequency rfid security tags|disposable high frequency rfid tags